

Get Cyber Essentials without the guesswork
Cyber ‘Cyber Essentials’ standard and meaningfully more secure — without guesswork, box-ticking, or last-minute panic. We don’t just help you pass. We make sure the controls actually work in your environment.
✔ Certification confidence
✔ Clear remediation
✔ No surprises on assessment day
Cyber Essentials Assured
Cyber Essentials is a UK government-backed scheme which certified that businesses have a baseline set of security protections against common cyberattacks. They Certification is focussed on five key areas: firewalls, secure configuration, user access management, malware protection, and patch management. It helps businesses secure data, reassure customers, and often to quality for UK government contracts.
The certification requires that you complete a self-assessment questionnaire to describe the systems, or controls, your business in place for each of five focus areas. Once complete the assessment is sent to the certification body for review. CyberSmart Technologies has partnered with a top-tier IASME Certification Body (CB) to perform your assessment and issue your certification.
Although this is a basic certification, the assessor will require comprehensive details of your assets, patching and updates process amongst others.
Most businesses don’t have comprehensive documentation operating system and browser versions for each device. CST offers comprehensive
Cyber smart
This is preparation and certification bundle.
Our Cyber Essentials Assured service provides three levels of support…
Self-prepared (0h)
€495
✔ Overview Call
✔ CyberEssentials Assessment
✔ Direct communication with assessor
Structured (4h)
€995
✔ Kickoff & Planning Call
✔ CyberEssentials Assessment
✔ Direct communication with assessor
✔ Inventory Management Pack
✔ 4 hours of Consultancy
Substantial (8h)
€2,095
✔ Orientation Call
✔ CyberEssentials Assessment
✔ Direct communication with assessor
✔ Inventory Management Pack
✔ Security Policy Jumpstart Pack
✔ 8 hours of Consultancy
Win Business
Cyber Essentials is increasingly a commercial requirement, not a technical one. It can:
- Unblock government and public-sector contracts
- Satisfy baseline due diligence for suppliers
- Reduce friction in customer security questionnaires
- Signals seriousness to partners and insurers
Importantly:
It iss recognisable outside IT.
A non-technical buyer understands what Cyber Essentials represents — that alone has value.
Mitigate real attacks
Cyber Essentials focuses on the exact failure modes attackers exploit most often:
- Unpatched systems
- Weak or reused credentials
- Over-privileged access
- Misconfigured endpoints
- Commodity malware
These aren’t theoretical risks. They account for the majority of:
- ransomware incidents
- account takeovers
- business email compromise
- lateral movement after phishing
Cyber Essentials doesn’t try to stop nation states. It stops the attacks that actually happen to businesses like ours.
That’s why it works.

Flex your Security Muscles
A forcing function for operational hygiene
One of the most underrated benefits:
Cyber Essentials forces decisions you’ve probably been avoiding.
It flushes out:
- undocumented systems
- inconsistent admin access
- legacy endpoints no one owns
- “temporary” exceptions that became permanent
Even organisations that fail the first time usually come out meaningfully more secure..

Build Foundations
One of the most underrated benefits:
Cyber Essentials forces decisions you’ve probably been avoiding.
It flushes out:
- undocumented systems
- inconsistent admin access
- legacy endpoints no one owns
- “temporary” exceptions that became permanent
Even organisations that fail the first time usually come out meaningfully more secure.
An Unfair Advantage
From a risk-economics perspective, Cyber Essentials is unusual:
- Narrow scope
- Clear controls
- Low implementation cost
- High impact on attack success rate
You’re not buying:
- a platform
- a toolset
- or ongoing licence sprawl
You’re buying:
- control discipline
- configuration hygiene
- access sanity
Few security investments punch this far above their weight.

Your staff are your best defence
How Cyber Essentials Assured Works..

Build Your Campaign
SoSafe Smart Phishing Simulation provides over one hundred choices of phishing emails. Each template is automatically customised to your business brand, domain and location. Each template targets specific psychological tactics, and has an associated micro-learning page to explain the ‘why’ each time a user clicks.
We will help you build a campaign of emails which suits your business. Together, we’ll choose a set of simulation emails known as a campaign, which carefully balance hyper realistic attacks and business realities. We often work with HR and Internal Communications teams to achieve the right tone for your business.
Although there’s a huge variety of templates available, you can also to create and craft your own phishing emails to match specific scenarios or the latest threats observed in your environment.
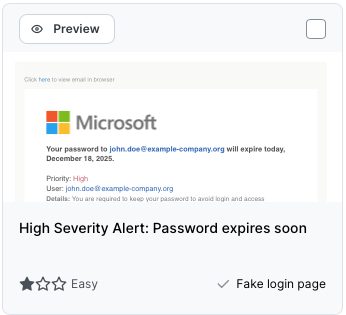

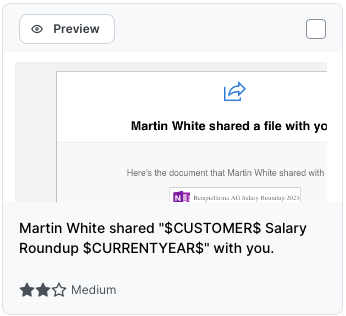
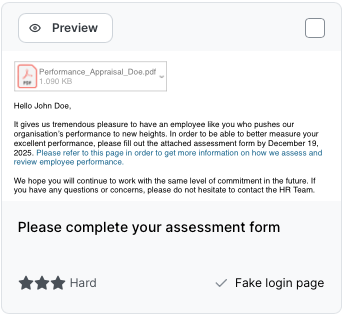
Pre-Assessment
Nobody likes surprises. Security awareness works best when your staff get advance notice of what the Phishing simulation campaign. CyberSmart Technologies will share templates for emails to your staff which set the scene and tell the story of ‘why’ you’ve taken this step.
Phishing simulations work on trust. Our goal is to recruit advocates who will embrace and engage fully in the simulation. We will create communications which show your staff how valuable their assistance and how they can make a significant contribution to your cyber security. We’ll communicate the goal of active training rather than testing, and that mistakes in simulation are expected as part of their learning journey.
We will let your staff know what’s in it for them too. They’ll acquire a set of cyber skills that they can apply to friends and family ones to help keep their loved ones safe.

Tools Of The Trade
SoSafe provides a Phishing reporting button which integrates into all email clients. We’ll deploy this button to your users so that they can report real and simulated phishing emails.
The Report Phish button is a tool you want your users to use at all times. If the reporting email isn’t a simulation, your Security team will receive a heads up. When your staff regularly use the Phish report button, so’ll know that Phishing detection has been embedded in the culture of your business.
CyberSmart Technologies also help you import your users from Entra ID using SCIM , or via CSV import. We’ll also user allow-listing and DMI to ensure the test emails reach the intended mailboxes.
Launch & Learn
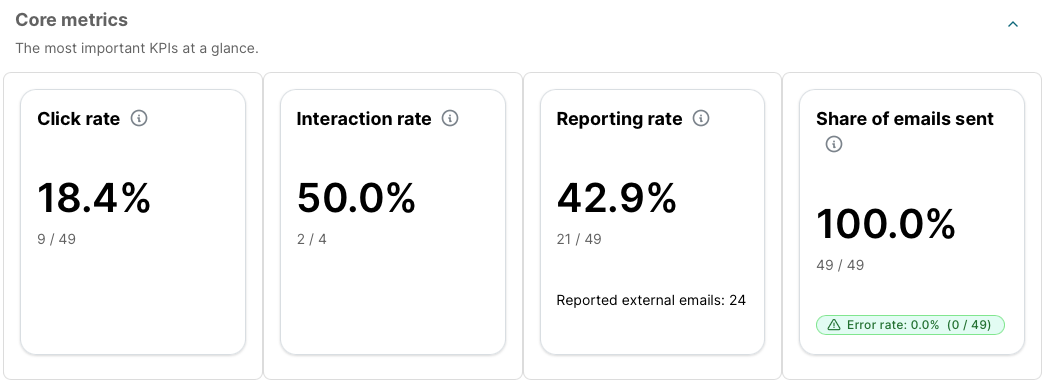
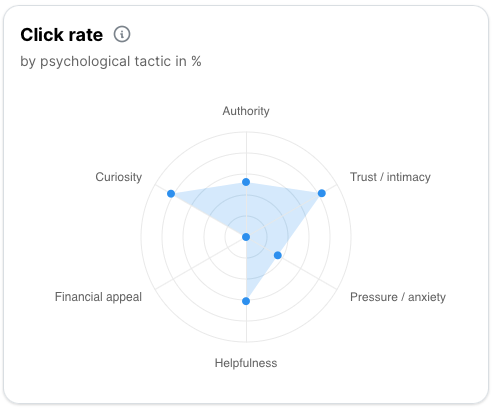
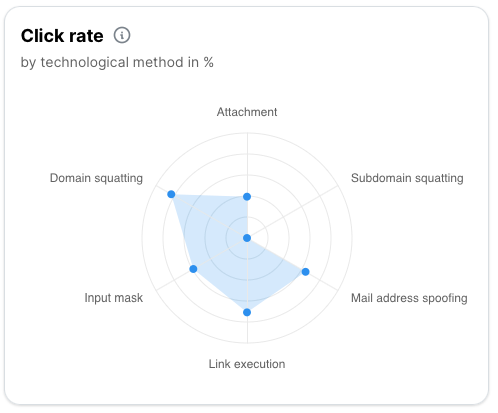
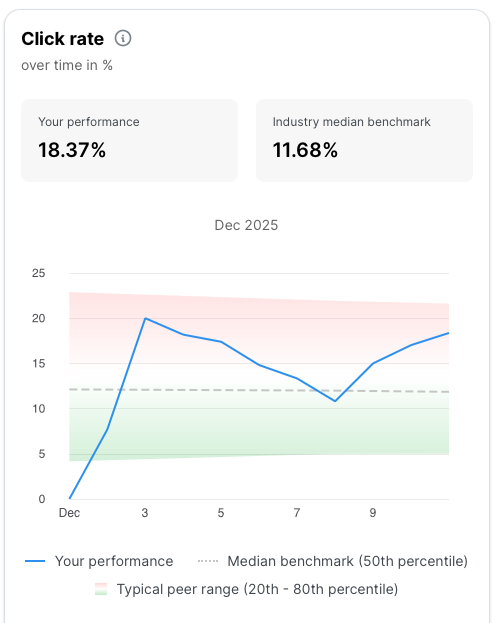
It’s launch time! You can immediately use the metrics and analytics to verify your simulation messages are being successfully delivered. You’ll see detailed metrics on overall stats, per-template, per-tactic and per-difficulty level. If your privacy agreement allows, you can even get a breakdown of each action on a per-user basis.
Refine
Once you campaign is live you’ll build an idea of how your users are responding and what motivates them. You can use this data to tune and refine your campaign, changing the tactics, or swapping under performing or overly difficult templates.
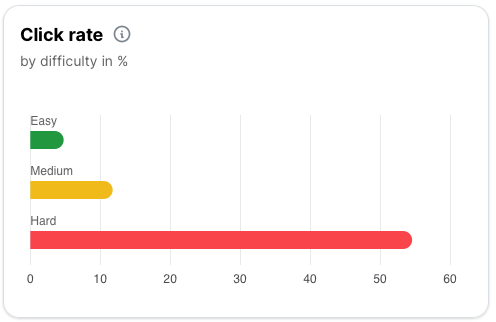
Report
We’ll arrange a close-out call to walk through the campaign and ensure you understand the findings and recommended improvements. All of the data required to provide board-level or auditor level reports are easily downloaded from the portal in PDF, CSV & XLSX formats.
CyberSmart Technologies provides a managed service where we provide continuous support via a dedicated account manager. We’ll meet your security team every quarter and share our analysis and recommendations, tune your campaign and advise on how to maximise the SoSafe platform to deliver the best security outcomes.
We can also prepare targeted in person and remote training sessions with your staff. We’ll use the data your team has generated. The training will highlight where they’re doing well and give focussed training on the topics where which they find most challenging.
Get in touch with us to discuss
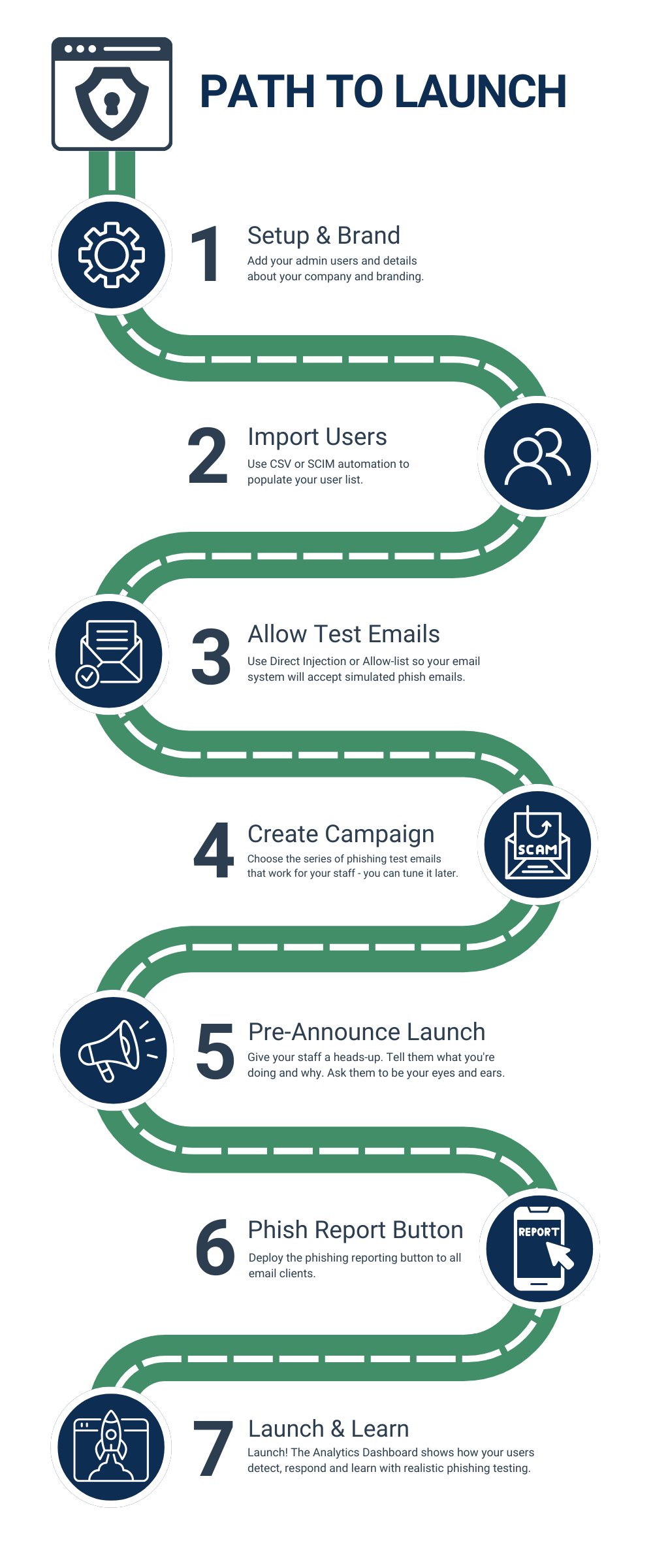
How we deliver
SoSafe provides an interactive preflight and launch checklist – built right in to your SoSafe admin portal. CyberSmart Technologies follows this ‘path to launch’. If we hit any speed bumps, we can quickly adjust course and get your campaign launched on time.
Frequently Asked Questions
Does Cyber Essentials Protect me from Ransomware?
Cyber Essentials (CE) will really strengthen your protections against ransomware, with a strong focus on upgrading and protecting your devices. However, CE is missing one critical aspect of ransomware protections – Ransomware Protected Backups. All the cyber essentials ‘controls’ are extremely useful, but you should also do a review of how your data is backed up and how those backups are protected.
We know the locks on our doors will delay a burglar, but not defeat them. It is produce to assume an attacker could breach your defences eventually also. The ‘assume-breach’ approach is a much more resilient approach to ransomware. Where are your backups, are the backups themselves protected from ransomware, how can you self-recover your data, and how quickly.
Can I see reports on phishing simulation results and prove risk reduction?
Yes, SoSafe provides real-time analytics dashboards which tracks key metrics such as: click rates, report rates, false positives, and user risk scores. You can segment the results by department, region, or custom groups; and identify top performers and areas needing extra support.
Do you offer Security Awareness Training?
Yes, we also offer sophisticated online Security Awareness Training(SAT) through our partner SoSafe.
How do phishing simulations contribute to enterprise security?
Phishing simulations contribute to enterprise security trough the following metrics:
- Reduced SOC workload as false-positive reports fall and true-positive alerts rise
- Lower breach likelihood & cost through reduced click rates and faster reporting
- Actionable risk visibility at the user and department level, guiding targeted interventions
- Zero training fatigue with adaptive frequency and real-time learning pages
- Compliance evidence via detailed, time-stamped reports.
Can simulations be customised to different departments?
Yes, the Premium plan enables targeted campaigns tailored to user’s role, location, and prior behavior to realistic attack scenarios—finance teams receive invoice fraud, developers see code-repo lures, executives face BEC attempts. Targeted content boosts relevance, sharpens instincts, and surfaces genuine risk by department or region.
Are you Ready to Strengthen Your Cybersecurity?
If you still have questions, you can reach us by email or arrange a chat.
